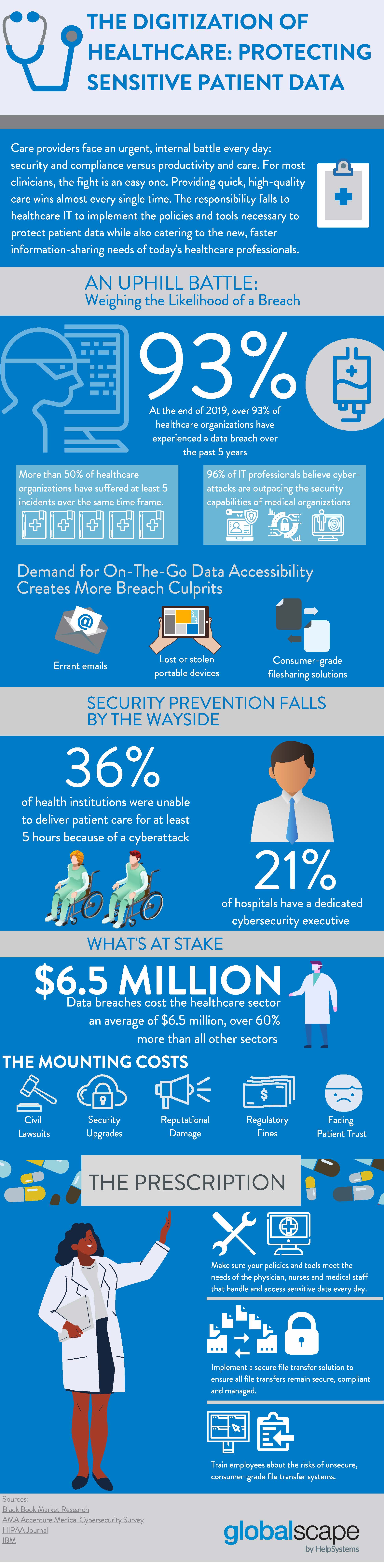
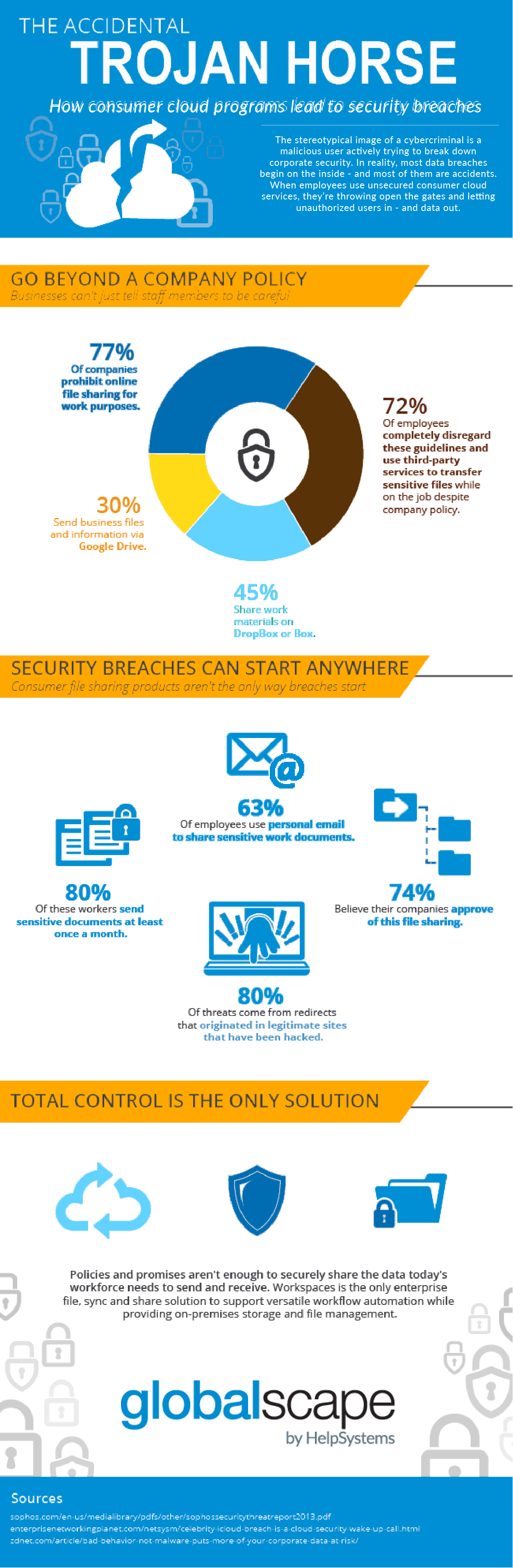
Business Continuity Planning for Your Critical Workflows
Downtime is no longer unavoidable with active-active high-availability solutionsBusiness managers know that providing their employees with constant, seamless access to their company’s data and applications is critical to success. ...